New Linux-Based Variant For AvosLocker Ransomware Aims At VMware ESXi Servers
AvosLocker, an emerging ransomware gang has added Linux system encryption to extend its latest malware variants. The recent variants are suspected to target VMware ESXi virtual machines.
The actual victims of the Linux variant of the AvosLocker Ransomware are however still unidentified. According to BleepingComputer, “While we couldn’t find what targets were attacked using this AvosLocker ransomware Linux variant, we know of at least one victim that got hit with a $1 million ransom demand.”
The Incidence
In November 2021, the AvosLocker gang revealed their latest ransomware variants, AvosLinux and Windows Avos2 while warning affiliates against attacking CIS/post-soviet websites.
In their advertisement, they wrote, “Avos2 / Avoslinux has the best of both worlds: High performance and high amount of encryption compared to its competitors”.
Other ransomware operations that support Linux and ESXi servers are Mespinoza, Babuk, HelloKitty, and RansomExx/Defray. The Linux variants of renowned ransomware enable intruder gangs to target a wide range of organizations, specifically those using ESXi servers.
How The Ransomware Gang Works
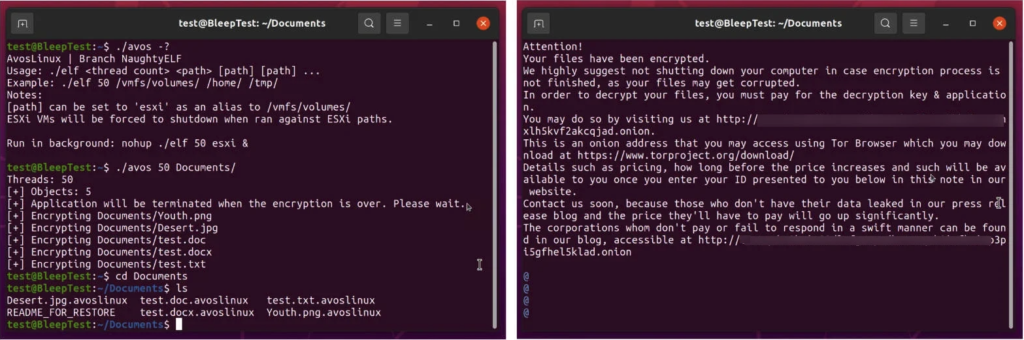
When AvosLocker gets installed on a compromised Linux system, it wiill run the following command:
esxcli –formatter=csv –format-param=fields==”WorldID,DisplayName” vm process list | tail -n +2 | awk -F $’,’ ‘{system(“esxcli vm process kill –type=force –world-id=” $1)}’
This command aims to shut down all ESXi machines on the server. Further, the ransomware will affix the .avoslinux extension to all encrypted files. The AvosLocker gang leaves ransom notes warning the victims not to shut down their systems to prevent file damage. The victims are further instructed to visit a TOR (onion) site for further information on how to pay the ransom.
Image Source: BleepingComputer
AvosLocker is a new gang that first emerged in the threat landscape during the summer of 2021. Initially, it called for ransomware affiliates to join their Ransomware-as-a-Service (RaaS) operation.
In December, the ransomware gang accidentally hit a US government entity. Fearing the police, it released a free decryptor to prevent any loss to the government authorities.
If you enjoyed this post, you will undoubtedly enjoy this one as well –
- Microsoft Released Emergency Fix for Remote Desktop Issues in Windows Server
- AWS Prolonged Outage Brings Internet At A Standstill
- GoDaddy Data Leak Hints Users Trust Is At Stake
- Rubrik Announces Azure-based New Data & Security Ransomware