
MOVEit Data Breach: Hacker with Alias “Nam3l3ss” Leaked Data of 760K Employees
After Amazon data breach, another breach from six organizations, via MOVEit flaws exploitation, occurred. The data was leaked on BreachForums on Monday by Nam3l3ss threat actor.
As per the latest data breach news via MOVEit Flaws, a hacker with alias Nam3l3ss has leaked the data of more than 760k employees from major organizations on a notorious hacking site BreachForums on Monday.
Around 3 weeks earlier, threat actor Nam3l3ss posted more than 2.8 million lines of employee data stolen from tech giant Amazon along with other 25 major organizations by exploiting MOVEit vulnerabilities.
How Was the Breach Disclosed?
Atlas Privacy operates databreach.com, it allows people to check their data is breached and help them to remove it from internet. The service’s initial analysis of the data Nam3L3ss disclosed that it exposes hundreds of thousands of employees’ names, phone numbers, email addresses, job addresses, employee badges, job titles, and usernames.
Which Organization is Affected?
The data was breached from 760k employees working at Xerox, Koch, Nokia, Bridgewater, Bank of America, and Morgan Stanley. All these firms were listed on BreachForums on Monday as per The Register.
The Data Breach Details
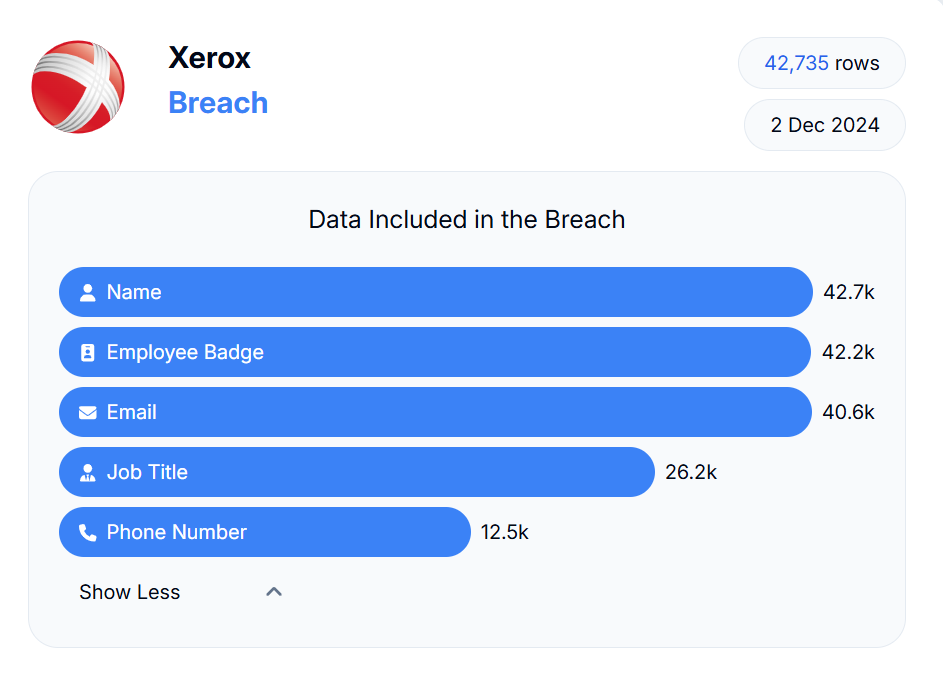
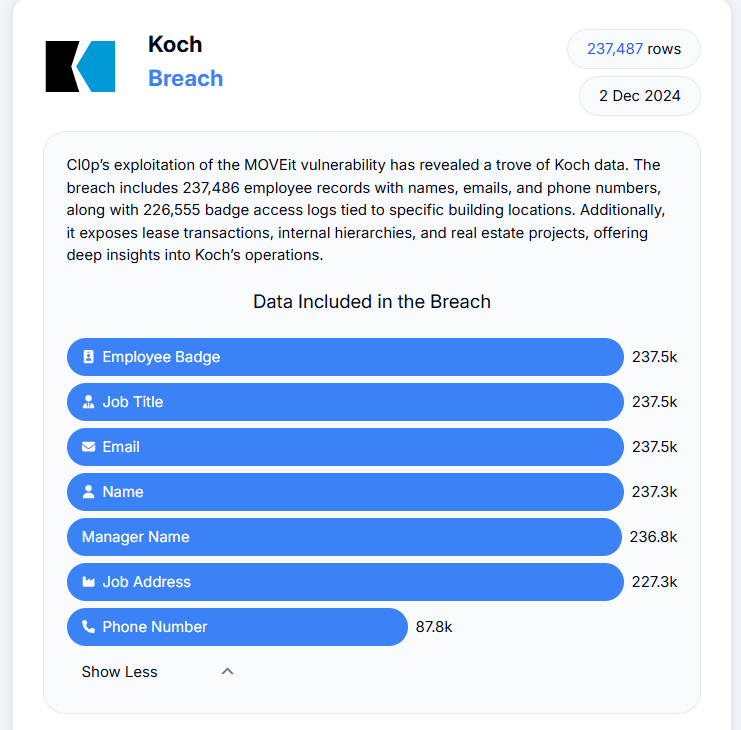
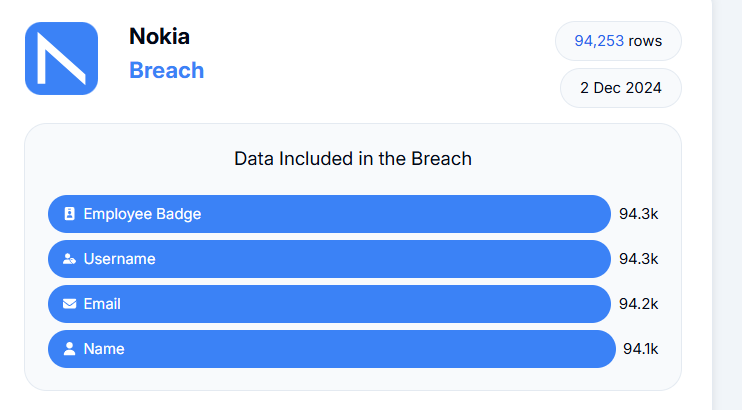
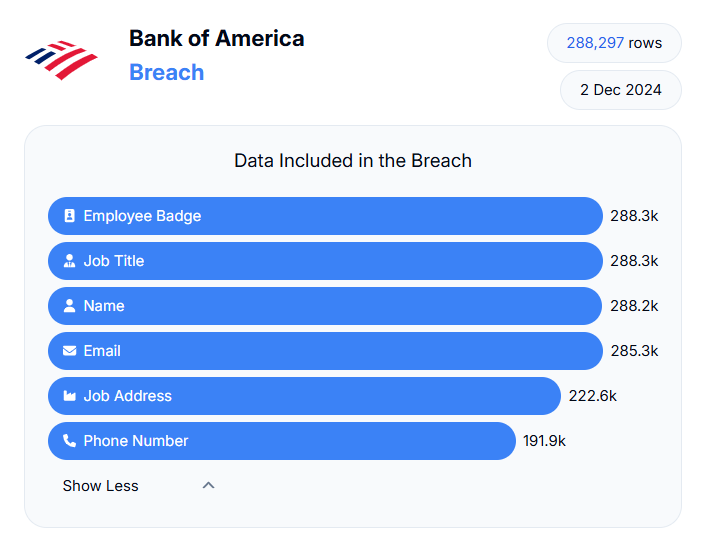
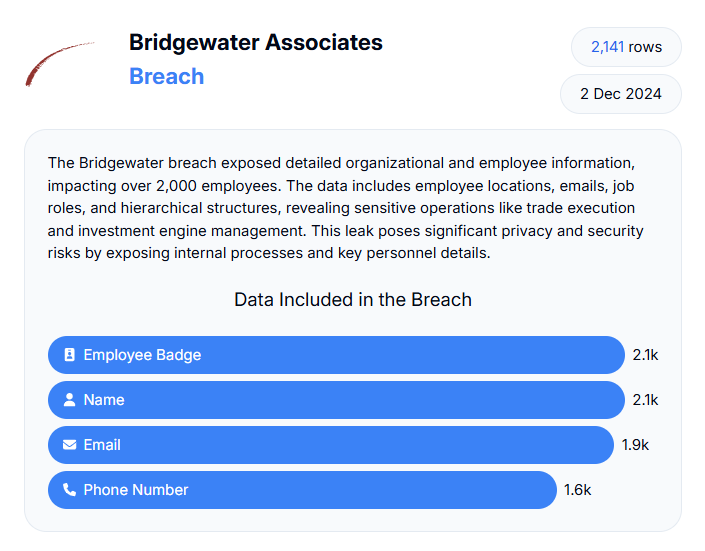
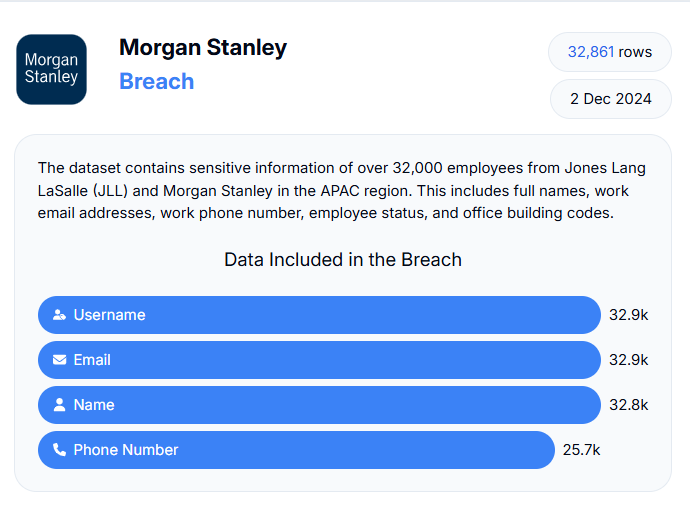
Image source: https://databreach.com/breach
Zack Ganot’s, Chief Strategy Officer for Atlas Privacy, Statement
“This data is a goldmine for social engineering. Knowing exactly what employee sits on, which team, who they report to, what their badge number is, what building they work in, their organizational email and phone number – this is some wild stuff for an attacker looking to exploit an org.”
“This type of data provides threat actors with a detailed organizational map, making it valuable for social engineering attacks. Some breaches also contain supplementary information, such as real estate lease records or project documents, though these appear less substantial”
Further Zack Ganot told The SecurityWeek, “we believe the data originates from the Cl0p ransomware group, who frequently exploit vulnerabilities like MOVEit to exfiltrate and publish sensitive data as part of their extortion campaigns. It’s likely Name3l3ss dug through terabytes of dark Web data and repackaged it for wider consumption.”
