
200K WordPress Websites Vulnerable to Cyberattacks
Vulnerabilities identified in Anti-spam, Firewall by CleanTalk Plugin for WordPress. It has exposed many WordPress sites to unauthenticated cyber attackers to install malware.
In the latest WordPress news, Two critical vulnerabilities in WordPress’s Anti-spam plugin have affected the WordPress site. This Anti-Spam by clean talk was installed in over 200,000 Sites. These two flaws have exposed sites to cyberattacks.
This Anti-spam firewall vulnerabilities allows the attackers to have full control of the website without providing any username and password. It lets the attackers install any plugin, including malware.
Vulnerabilities Summary by Wordfence Intelligence
These two vulnerabilities are identified as CVE-2024-10542 and CVE-2024-10781.
CVE-2024-10542
The Spam protection, Anti-Spam, Firewall by CleanTalk plugin for WordPress is vulnerable to unauthorized Arbitrary Plugin Installation due to an authorization bypass via reverse DNS spoofing on the checkWithoutToken function in all versions up to, and including, 6.43.2.
Impact
This makes it possible for unauthenticated attackers to install and activate arbitrary plugins which can be leveraged to achieve remote code execution if another vulnerable plugin is installed and activated.
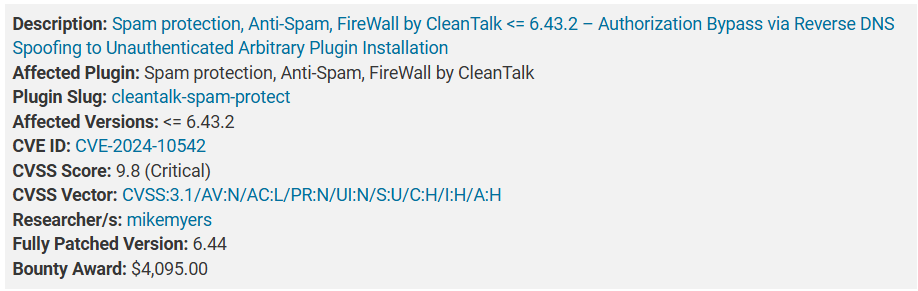
Image Source: https://www.wordfence.com/blog/2024/11/200000-wordpress-sites-affected-by-unauthenticated-critical-vulnerabilities-in-anti-spam-by-cleantalk-wordpress-plugin/
CVE-2024-10781
The Spam protection, Anti-Spam, Firewall by CleanTalk plugin for WordPress is vulnerable to unauthorized Arbitrary Plugin Installation due to a missing empty value check on the ‘api_key’ value in the ‘perform’ function in all versions up to, and including, 6.44.
Impact
This makes it possible for unauthenticated attackers to install and activate arbitrary plugins which can be leveraged to achieve remote code execution if another vulnerable plugin is installed and activated.
Image Source: https://www.wordfence.com/blog/2024/11/200000-wordpress-sites-affected-by-unauthenticated-critical-vulnerabilities-in-anti-spam-by-cleantalk-wordpress-plugin/
The Screenshot of Vulnerability (CVE-2024-10542) Severity Rating
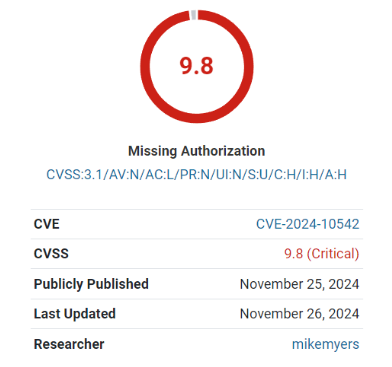
Image Source: https://www.searchenginejournal.com/wordpress-anti-spam-plugin-vulnerability-hits-200k-sites/533844/
When were the vulnerabilities identified?
30th October 2024
Wordfence received the submission for the Authorization Bypass vis reverse DNS spoofing vulnerability (CVE-2024-10542) in Anti-spam by CleanTalk on 30th October 2024 through the Wordfence Bug Bounty Program.
On the same day, Wordfence validated the report and confirmed the exploit. Wordfence users received a firewall rule to provide protection against any exploits that may target the first vulnerability.
They sent full details of the vulnerability to the vendor and the vendor after acknowledging the report, started working on a fix.
1st November 2024
The partially patched version, 6.44, of the plugin was released.
4th November 2024
The Wordfence threat intelligence team identified an Authorization bypass due to Missing entry check vulnerability (CVE-2024-10781) during patch review.
Again, Wordfence users received a firewall rule to provide protection against any exploits that may target the second vulnerability.
14th November 2024
The fully patched version, 6.45, was released.
29th November 2024
Users receive the same protection against the Authorization Bypass via Reverse DNS Spoofing vulnerability (CVE-2024-10542).
4th December 2024
Users will receive the same protection against the Authorization Bypass due to Missing entry check vulnerability (CVE-2024-10781).
